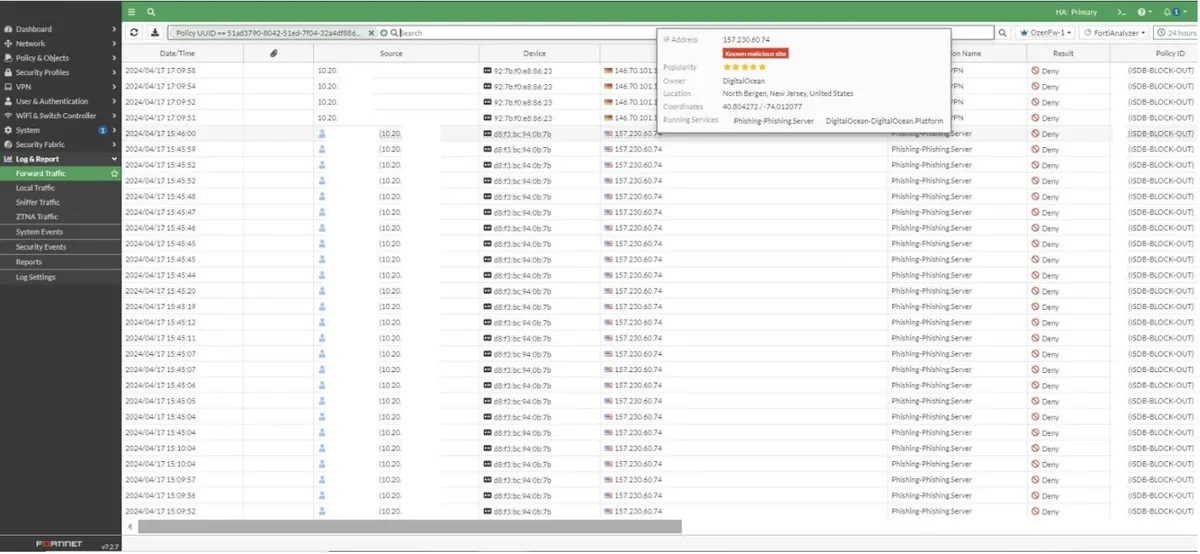
Fortigate Recommended WAN Block Rule
We will explain how to block internal users from dangerous IP addresses or known malicious hosts through a VIP. 1- Known malicious sites (Phishing, Botnet) 2- High risk service sites (TOR, proxy, P2P) 3- Unverified sites. 4- Known and verified secure sites (Gmail, eBay, Amazon...) 5- Social media (Facebook, X, TikTok...)
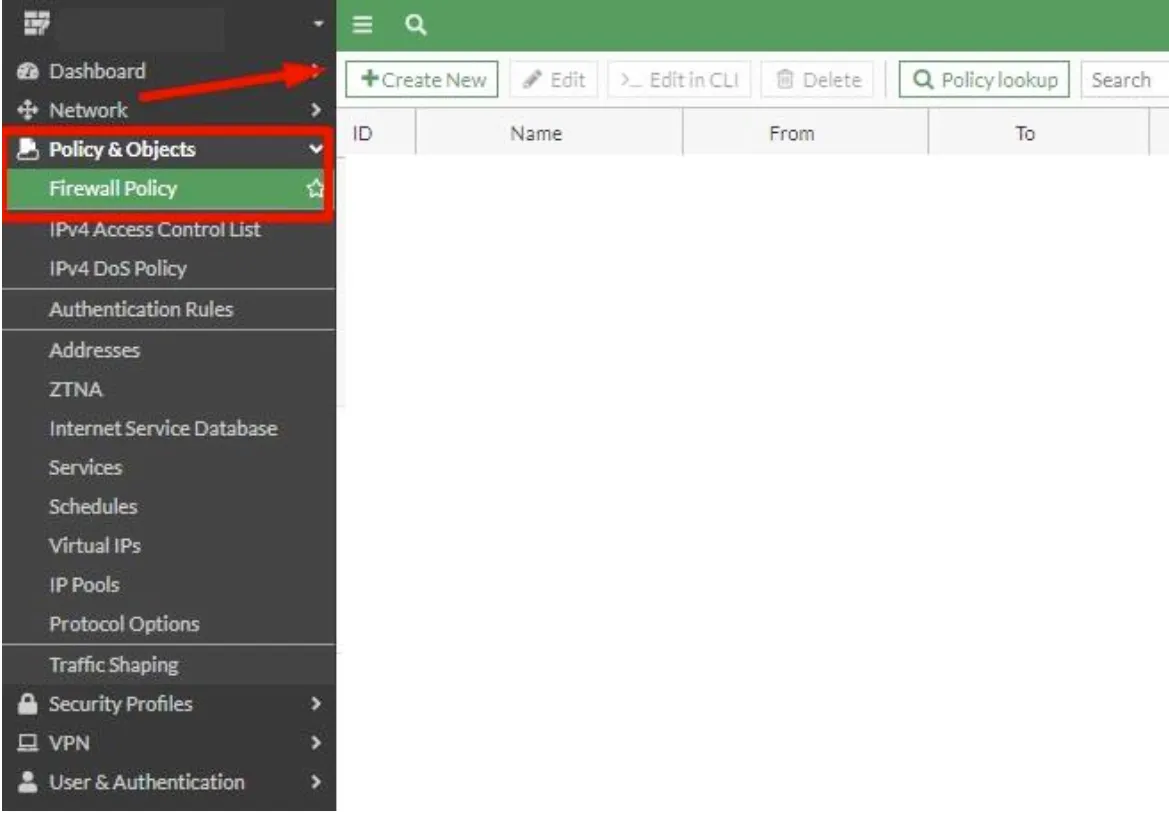
First, we go to the Policy & Objects > Firewall Policy tab and start creating our new rule.
Since our goal is to block threats, we will add the Internet Service Databases we mentioned in the image below to the Source section. If you wish, you can also block other services in the list. Blockchain-Crypto.Mining.Pool (Can only be added to the destination section.) Botnet-C&C.Server Malicious-Malicious.Server Phishing-Phishing.Server Proxy-Proxy.Server Spam-Spamming.Server Tor-Exit.Node (Can only be added to the source section) Tor-Relay.Node VPN-Anonymous.VPN
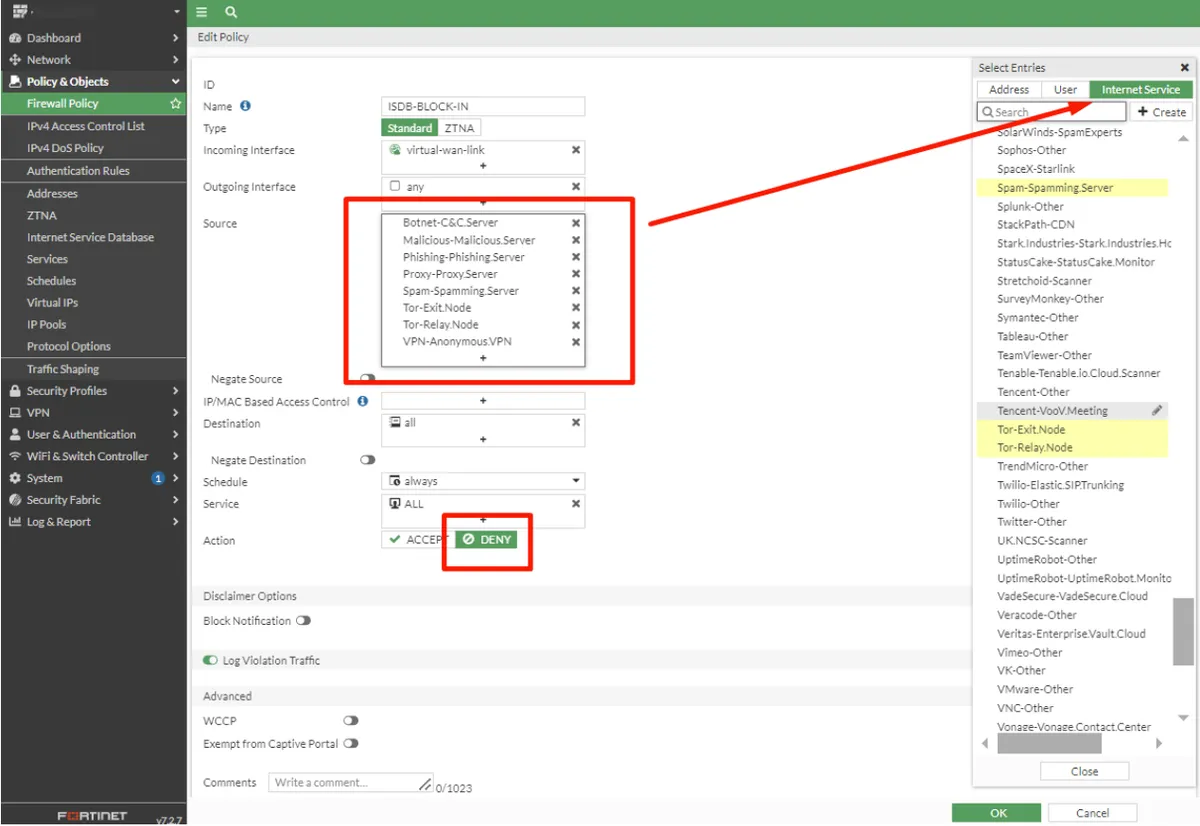
Due to the working logic of the rules, you need to move them to the top of the rules. Otherwise, the rule you wrote will not work. You should make the same rule for VIPs under the rule you wrote for WAN to Any. It will be to your advantage to create a VIP Group in the Destination section and include all of them.
Then we reverse the rule to prevent internal devices from accessing these databases.
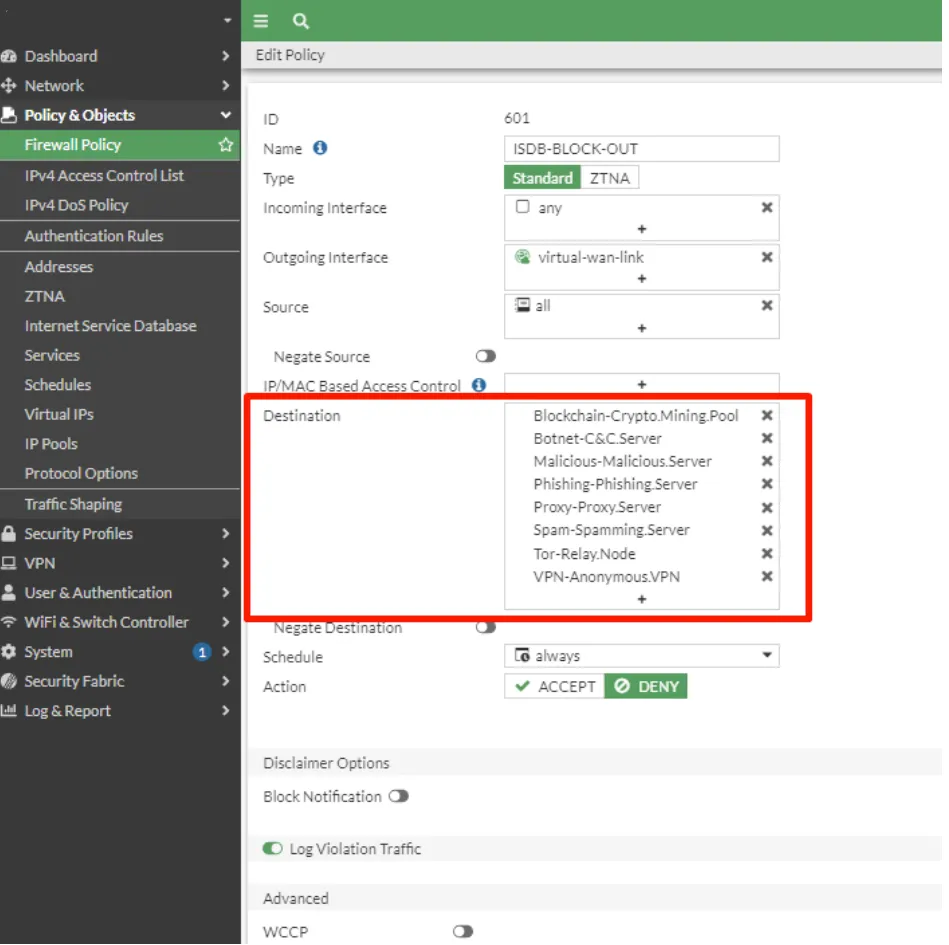
When our rules are completed, they should be as follows.
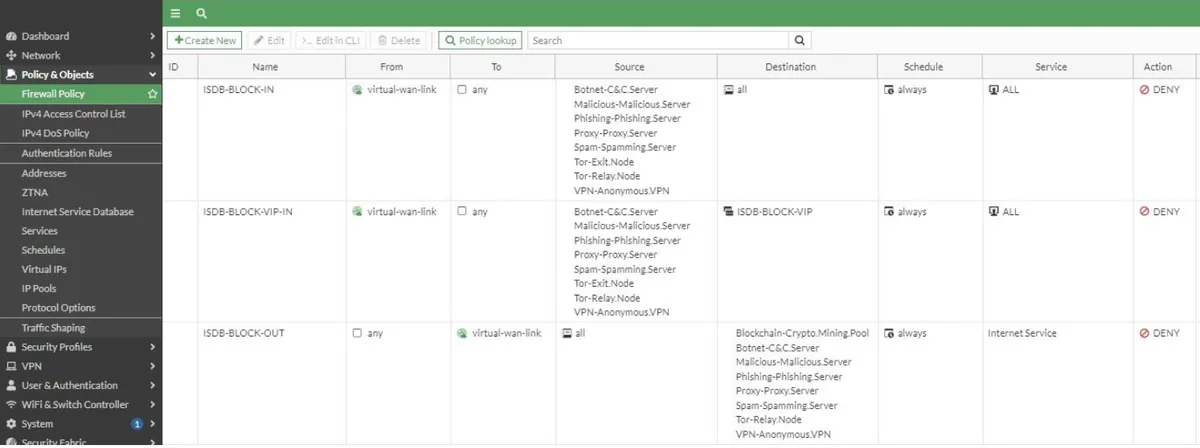
You can see sample notes for blocking below? Do you know that you can try the scenario we explained in this article on your own computer by purchasing the EVE-NG FULL Package at labimage.com.tr?