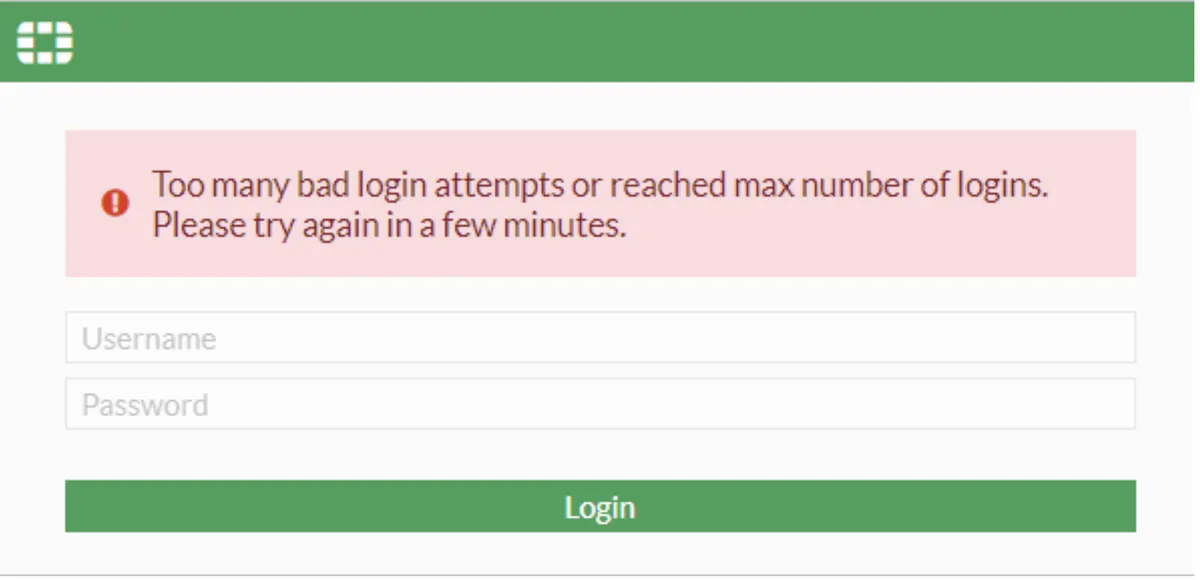
1. Preliminary Information
We can apply this scenario for situations where we have to open the Fortinet Panel login to the outside world, the same situation can be applied in the SSL VPN Web Interface. It should not be forgotten that, above all, in order to maximize security in normal situations, it is necessary to use Trusted Host and never open "https" for external access. Despite this, in cases where we have to, we can at least activate the feature below.
2.Installation
For this, we need to keep the IP addresses we will block in a pool; From the Fortinet Web Panel, from the menu on the left, we add an address group by clicking Policy&Objects --> Addresses-->Create New-->Address Group.
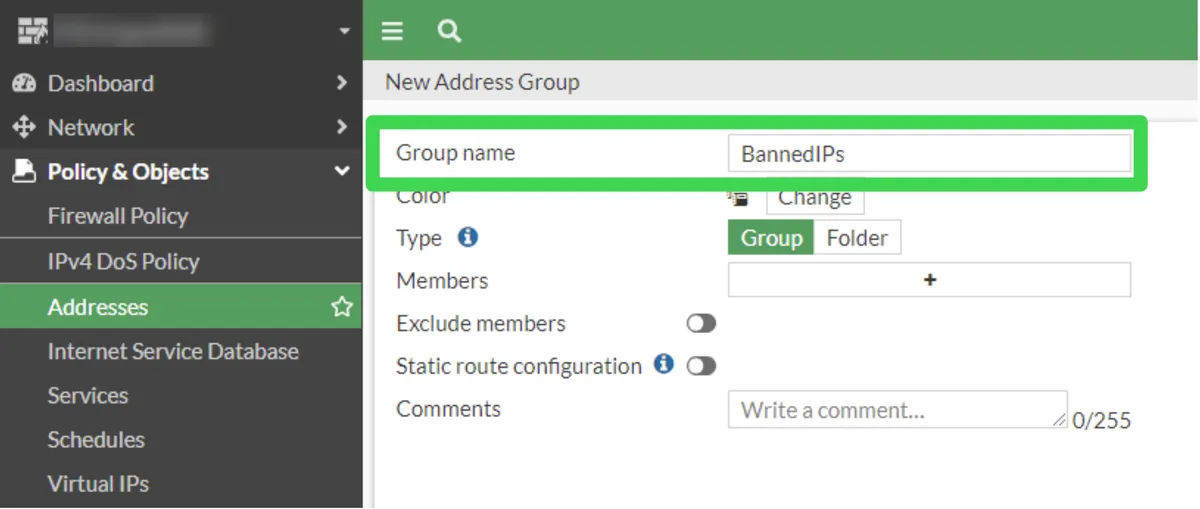
After creating our group, we connect to FortiNet's terminal by pressing the CLI icon in the upper right corner of the Fortinet Web Interface.
config system global
set admin-lockout-threshold 2 --> In this command we give here, we specify the number of unsuccessful login attempts after which the IP address will be banned. I say ban the IP address that tries to log in unsuccessfully after 2 times.
end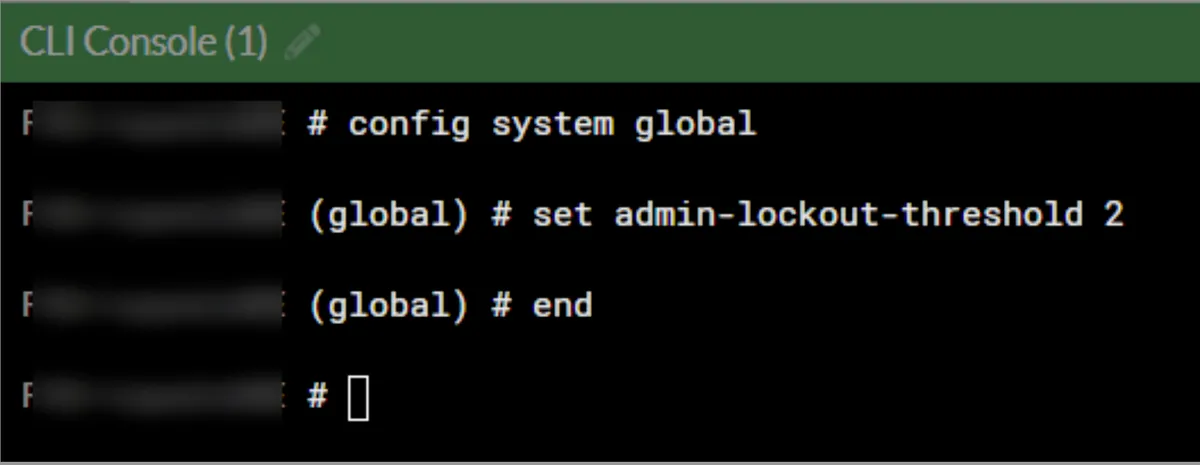
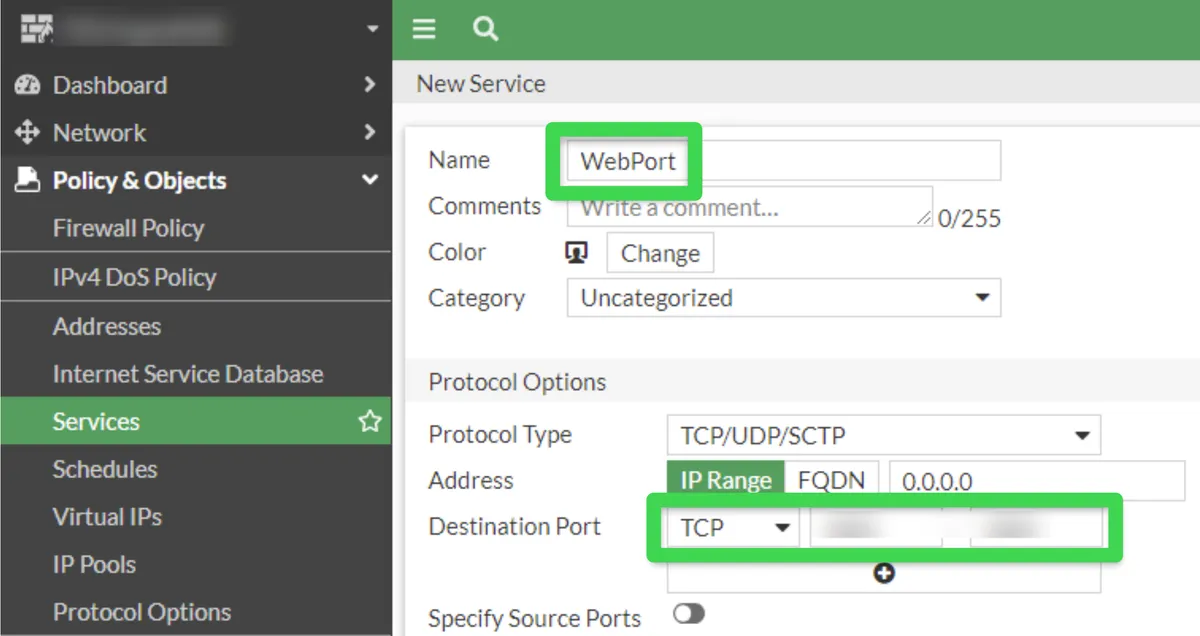
As the last step in this section, we create our service to use in local-in-policy by clicking Policy&Objects --> Services-->Create New from the menu on the left. The port we specify here is the port we use to access the Web Panel, we write this and create our service.
3. Creating Security Fabric Automation
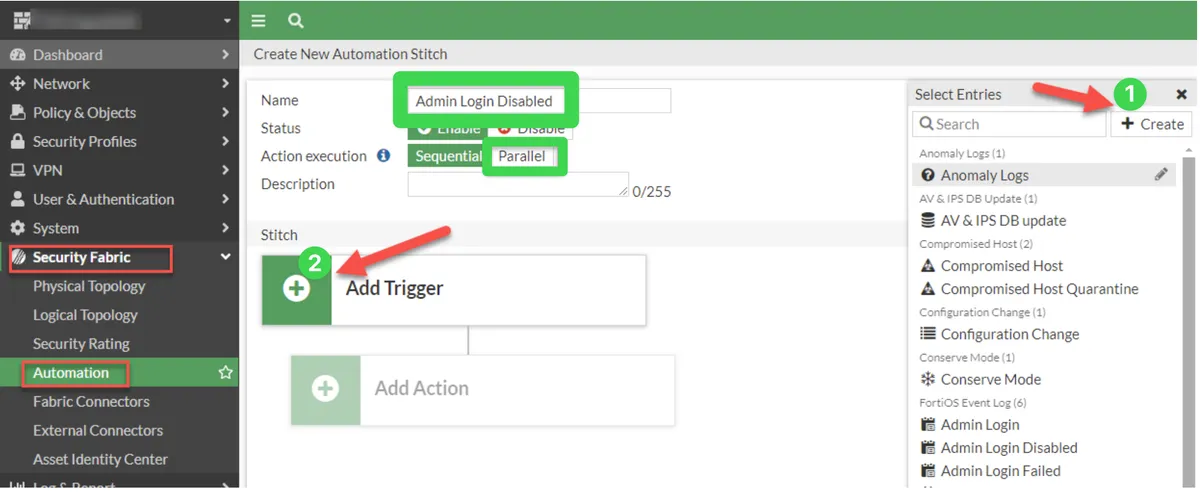
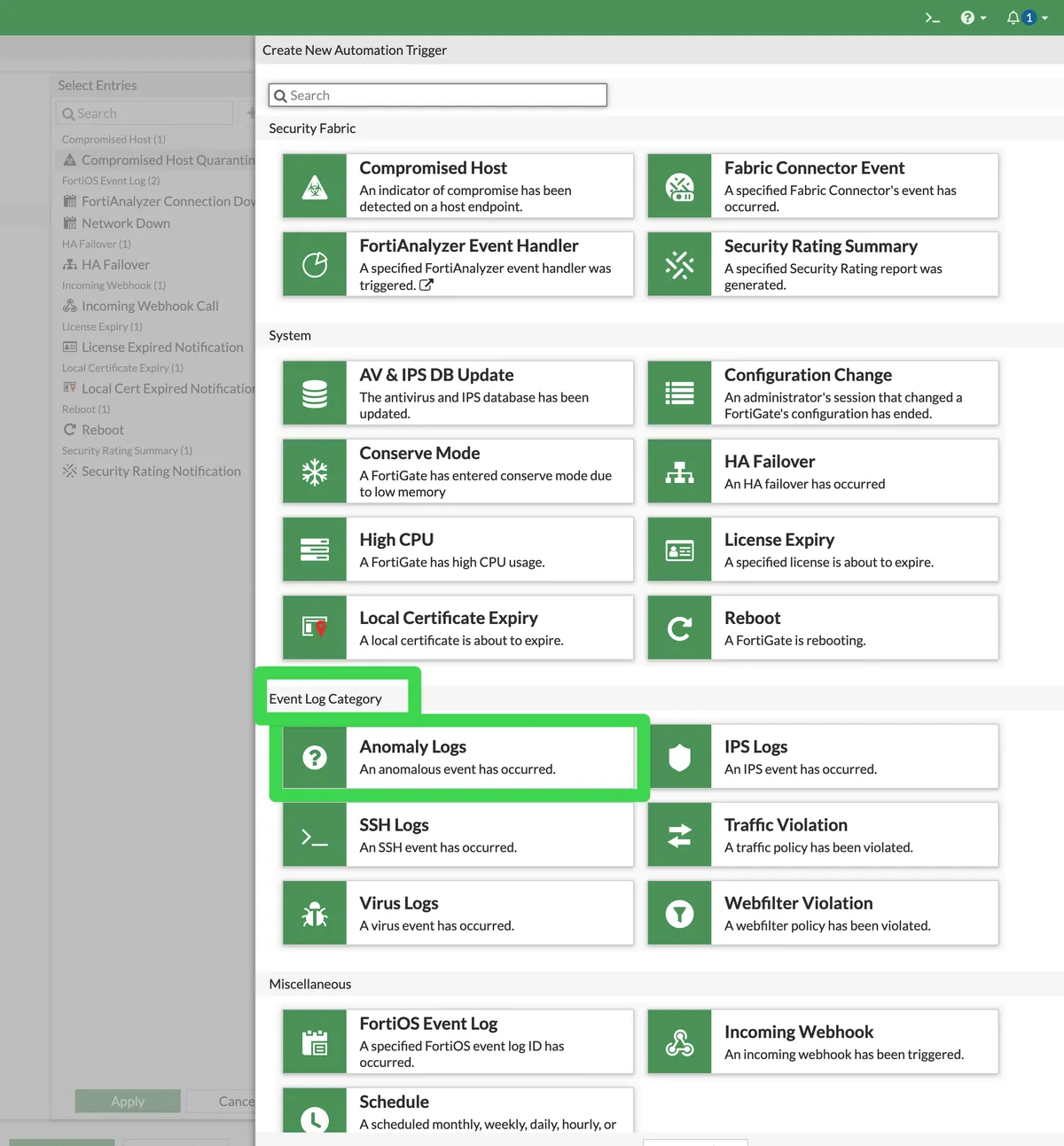
We call Security Fabric --> Automation-->Stitch-->Create New. We specify a name in the Name section. We select Action Execution Parallel. After clicking Add Trigger, we press the Create button from the Select Entries section on the right, select the "Anomaly Logs" section from the Event Log Category section, then give a name to this event in this section, and then select it as Trigger and complete this section.
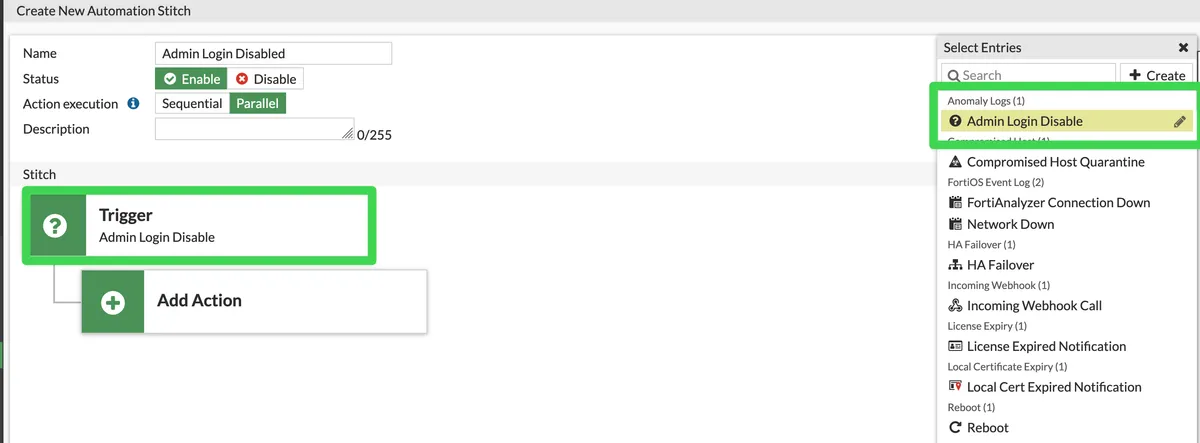
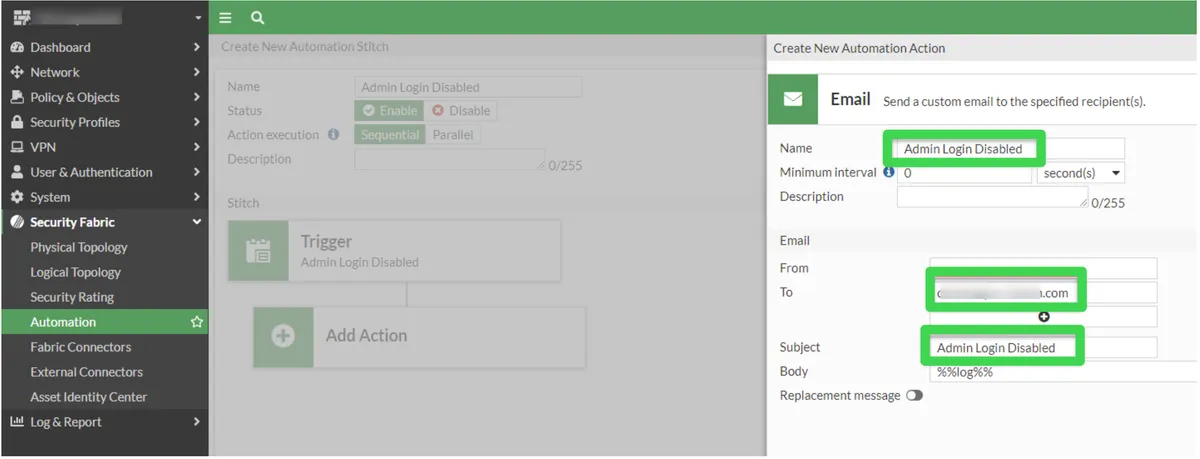
Add Action --> Click the Create button in the Select Entries section opened on the right and first select Email.
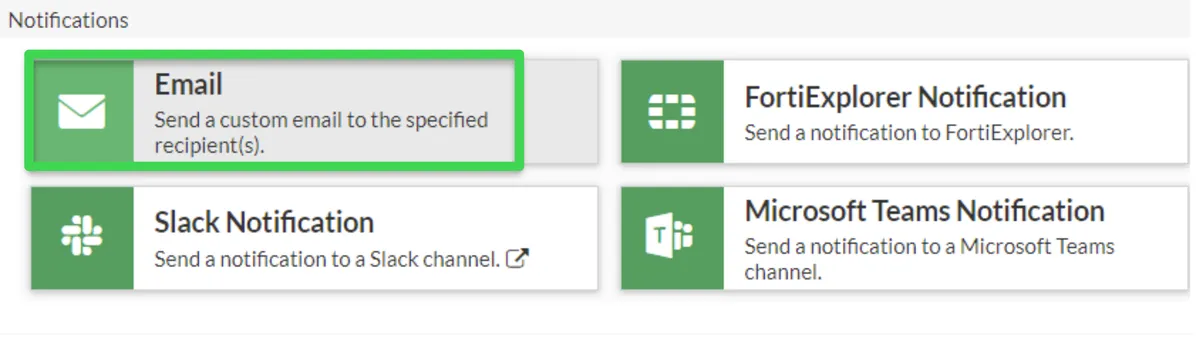
We determine a name for the mail scenario. In the To section, we write the e-mail address we will send and the subject of the e-mail and complete it.
We create another Action and this time, we select CLI Script from the Select Entries section opened on the right.
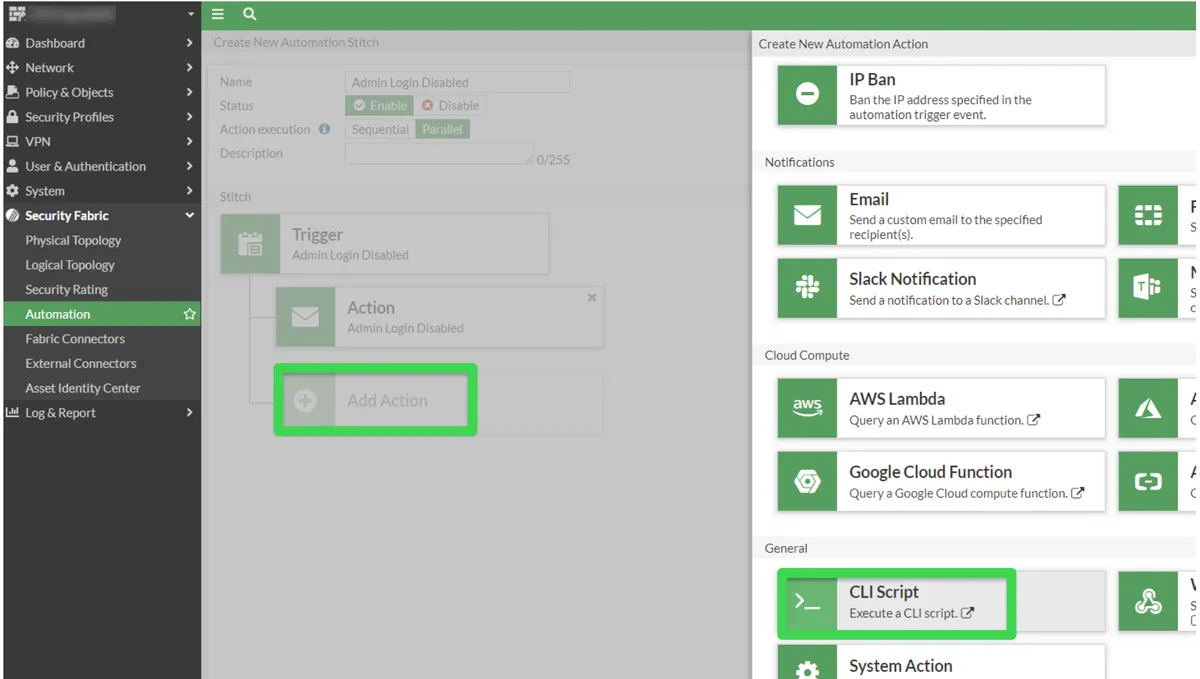
We give a name to the script we will create and then write our CLI commands in the CLI Script section.
config firewall address
edit %%ui%%
set subnet %%ui%% 255.255.255.255
next
end
config firewall addrgrp
edit BannedIPs
append member %%ui%%
next
endWe select super_admin in the Administrator profile section. The final form of the Automation we created is as follows.
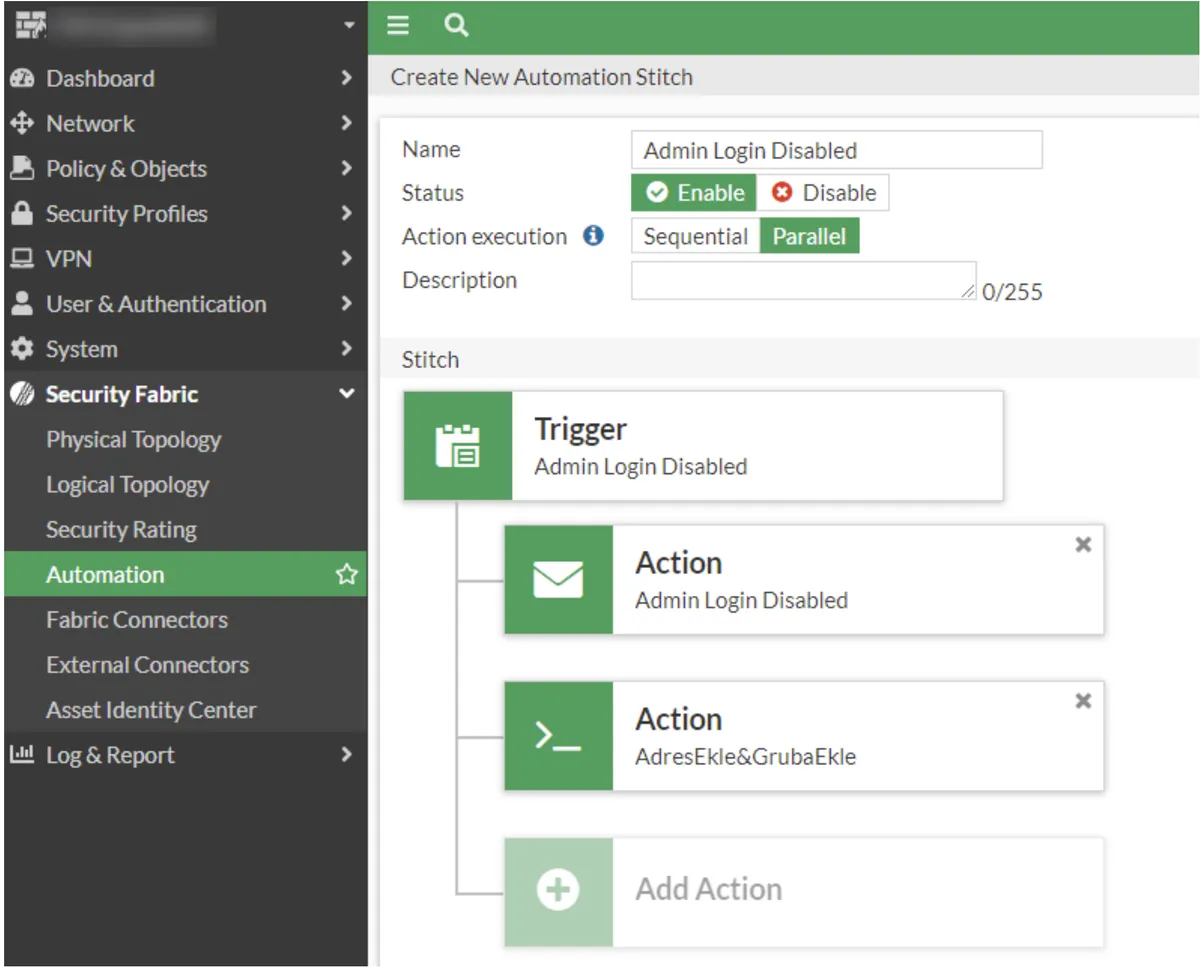
4.Policy Creation
Before performing Local-in Policy deny, we need to allow our own IP address with the ACCEPT command. For this, we use the Web port, which is our service port that we created in the first step. If we wish, we can turn off all services by clicking ALL. We would like to remind you that creating a service port is completely optional.
5.Creating an ACCEPT Rule for Our IP Address
config firewall local-in-policy
edit 1
set intf wan1
set srcaddr xxx.xx.x.x (Buraya ip adresimizi yazacağız)
set dstaddr all
set action accept
set service WebPort
set schedule always
set status enable
end6.Creating Deny Rule for Auto Ban IP
config firewall local-in-policy
edit 2
set intf wan1
set srcaddr BannedIPs (Daha önce oluşturduğumuz grup)
set dstaddr all
set action deny
set service WebPort
set schedule always
set status enable
end7. Final
When we complete the steps here in order, as you can see in the example below, the access of the IP address that entered the wrong password twice into the Fortinet Web Panel from outside will be automatically restricted and at the same time, an information e-mail will be sent to the e-mail address we have specified. You can use the same operations here in SSL-VPN Port scenarios.